Renewable energy sources, including solar power systems, are rapidly becoming essential elements of power grids throughout the world — especially in the U.S. and Europe. However, cybersecurity for these systems is often an afterthought, creating a growing risk to grid security, stability and availability.
New research from network security solution provider Forescout found an insecure ecosystem — with dangerous energy and national security implications. While each residential solar system produces limited power, their combined output reaches dozens of gigawatts — making their collective impact on cybersecurity and grid reliability too significant to ignore.
In the full report, Forescout reviews known issues and presents new vulnerabilities found on three leading solar power system manufacturers: Sungrow, Growatt and SMA. Forescout also discusses realistic power grid attack scenarios that could be executed and could cause emergencies or blackouts, and provides recommended risk mitigation actions for owners of smart inverters, utilities, device manufacturers and regulators.
Summary of findings
- Forescout cataloged 93 previous vulnerabilities on solar power and analyzed trends:
- There’s an average of over 10 new vulnerabilities disclosed per year in the past three years
- 80% of those have a high or critical severity
- 32% have a CVSS score of 9.8 or 10 which generally means an attacker can take full control of an affected system
- The most affected components are solar monitors (38%) and cloud backends (25%). Relatively few vulnerabilities (15%) affect solar inverters directly
- Due to growing concerns over the dominance of foreign-made solar power components, Forescout analyzed their common countries of origin:
- 53% of solar inverter manufacturers are based in China
- 58% of storage system and 20% of the monitoring system manufacturers are in China
- The second and third most common countries of origin for components are India and the US
- New vulnerabilities:
- Forescout analyzed six of the top 10 vendors of solar power systems worldwide: Huawei, Sungrow, Ginlong Solis, Growatt, GoodWe, and SMA
- Forescout found 46 new vulnerabilities affecting different components in three vendors: Sungrow, Growatt and SMA.
- These vulnerabilities enable scenarios that impact grid stability and user privacy
- Some vulnerabilities also allow attackers to hijack other smart devices in users’ homes
Impact on Grid Security
The new vulnerabilities, which have now been fixed by the affected vendors, could allow attackers to take full control of an entire fleet of solar power inverters via a couple of scenarios, as shown in the report:
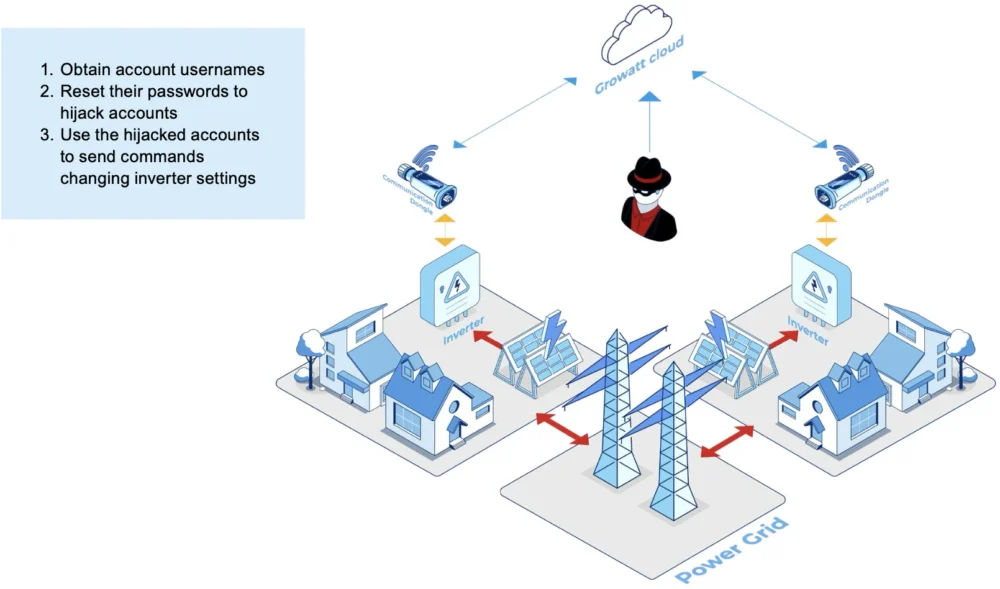 Once in control of these inverters, attackers can tamper with their power output settings or switch them off and on in a coordinated manner as a botnet. The combined effect of the hijacked inverters produces a large effect on power generation in a grid. The impact of this effect depends on that grid’s emergency generation capacity and how fast that can be activated.
Once in control of these inverters, attackers can tamper with their power output settings or switch them off and on in a coordinated manner as a botnet. The combined effect of the hijacked inverters produces a large effect on power generation in a grid. The impact of this effect depends on that grid’s emergency generation capacity and how fast that can be activated.

The example Forescout discusses in the full report is that of the European grid. Previous research showed that control over 4.5 GW would be required to bring the frequency down to 49Hz — which mandates load shedding. Since current solar capacity in Europe is around 270 GW, it would require attackers to control less than 2% of inverters in a market that is dominated by Huawei, Sungrow and SMA.
Recommendations
- Treat PV inverters in residential, commercial, and industrial installations as critical infrastructure:
- Owners of commercial and industrial installations should:
- Include security requirements in procurement
- Conduct a risk assessment when setting up devices
- Ensure network visibility into solar power systems
- Segment and monitor devices into their own sub-networks
- Device manufacturers should:
- Implement secure software lifecycle practices
- Conduct regular penetration testing
- Adopt security-in-depth strategies using web application firewalls
- Use third-party audits of communication links based on standards, such as: ETSI EN 303 645, Radio Equipment Directive (RED) and Cyber Resilience Act (CRA)
News item from Forescout